About Me
Hi, my name is Aamir Muhammad. I am actively learning and striving to expand my knowledge in the cybersecurity field. I am eager to explore various aspects of cybersecurity and gain practical experience to enhance my skills. Through dedicated self-study and possibly seeking out mentorship or relevant courses, I aim to build a solid foundation and eventually contribute meaningfully to the cybersecurity industry.
Skills
HTML | CSS | Visual Studio| Wireshark | Windows | Cisco
Network security
Risk management
Problem solving
Adaptability
Communication
Attention to detail
Featured Projects
HTB ACADEMY| Windows Event Log Analysis and Threat Detection
Developed a module dedicated to exploring Windows Event Logs to identify and analyze suspicious activities. Implemented techniques for monitoring and interpreting log data to enhance threat detection capabilities, contributing to improved security measures and incident response protocols.
Professional Certifications
My growing list of proprietary certifications.

Google Cybersecurity Certification| Issued 2024
CISCO Packet Tracer| CCNA Virtual Lab
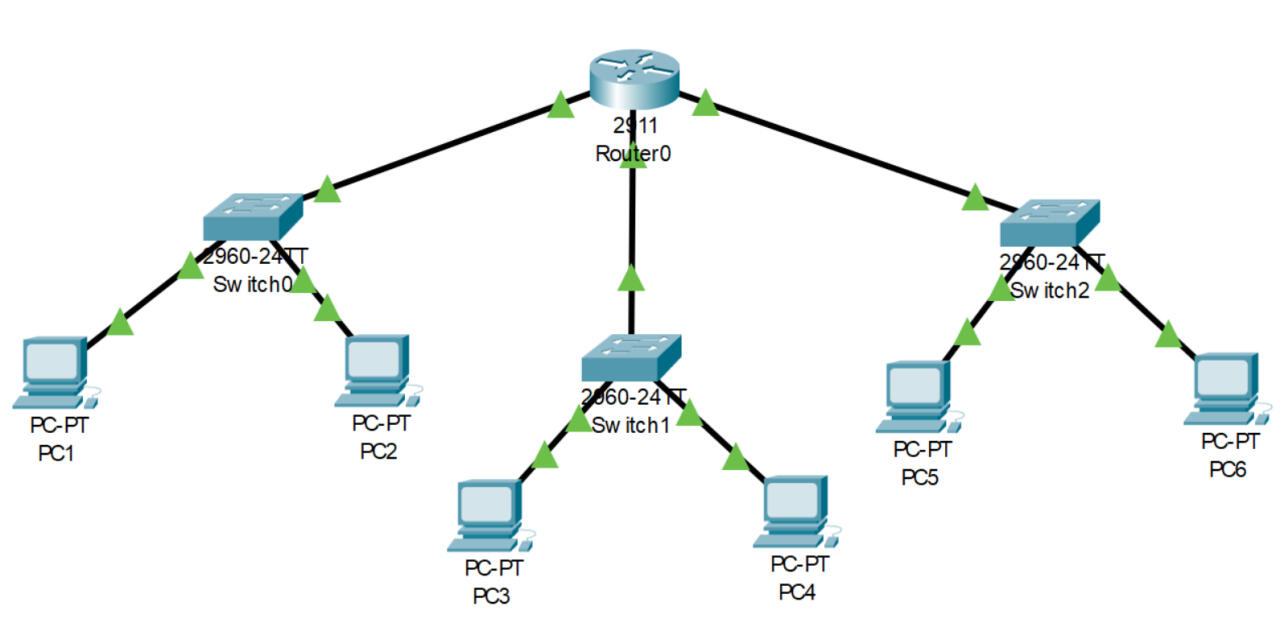
Scope
The project involves setting up a Cisco virtual network lab to provide a simulated environment for testing, developing, and refining network configurations. This virtual lab will support various network design scenarios, enabling comprehensive practice with Cisco technologies without the need for physical hardware. The scope includes installing network simulation software, creating a network topology tailored to client requirements, configuration of virtual devices, and documentation of the setup for ongoing use and analysis.Outcome
Upon completion of the project, the client will have a fully functional Cisco virtual network lab tailored to their needs. This lab will provide a realistic simulation environment for practicing and validating network configurations and designs. The outcome will include a well-documented network topology, detailed configuration files, and a set of test scenarios to evaluate network performance and reliability. The client will gain valuable insights into their network setup, enhance their ability to troubleshoot issues, and improve their overall network design and management skills.Problem Solved
The Cisco virtual network lab addresses several challenges faced by clients in network design and management. It eliminates the need for physical hardware, reducing costs and logistical issues associated with setting up and maintaining a real-world lab. By providing a simulated environment, the lab enables clients to test and refine network configurations safely and efficiently, without impacting live systems. Additionally, it offers a platform for hands-on learning and practice, helping clients better understand Cisco technologies and improve their network management capabilities.
HTB ACADEMY |Active Directory Implementation and Management
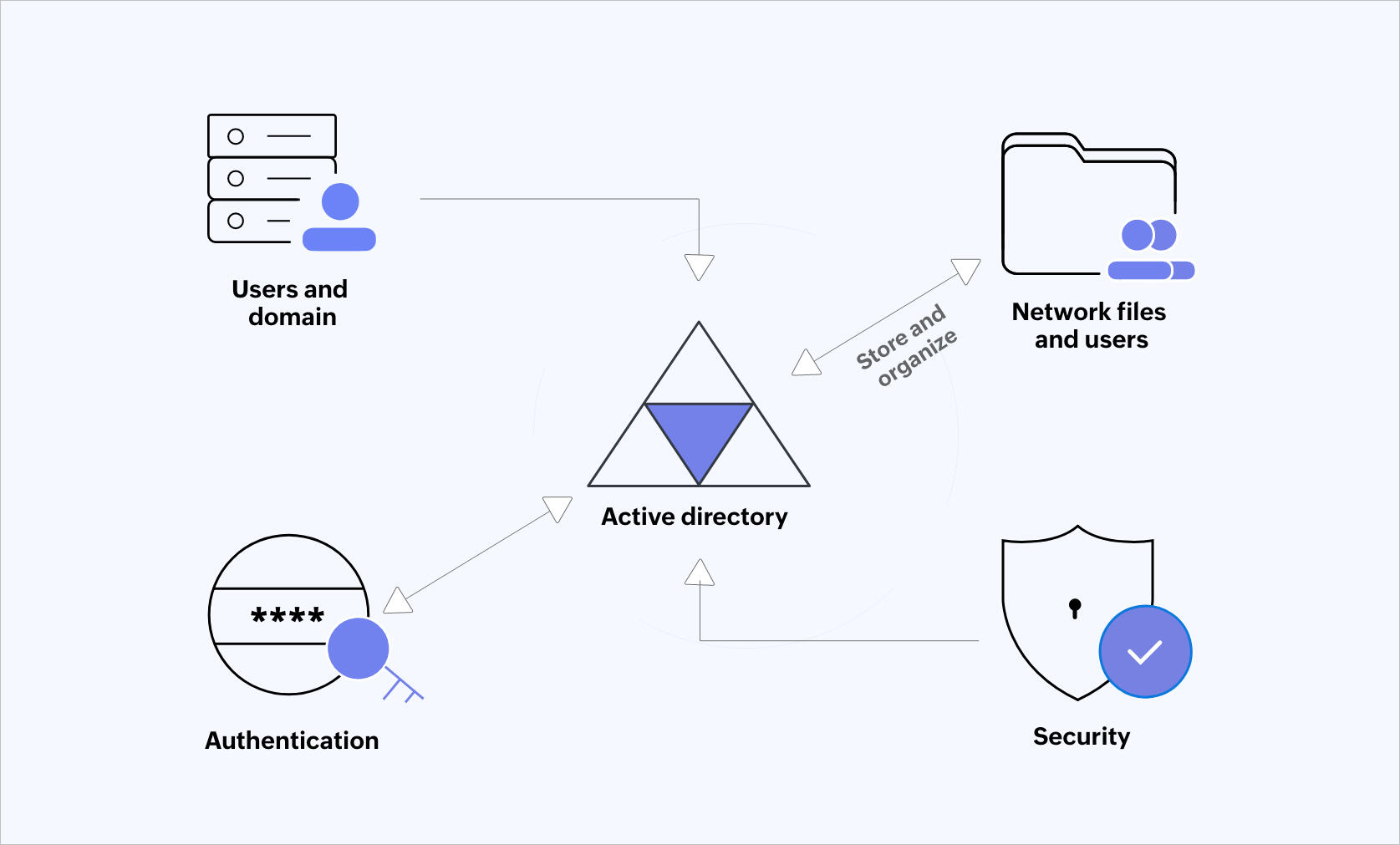
The HBT Active Directory project encompasses the design, implementation, and configuration of a robust Active Directory (AD) infrastructure for HBT. The scope includes setting up a centralized AD environment to manage user accounts, security policies, and network resources effectively. This project will involve configuring domain controllers, establishing organizational units (OUs), defining group policies, and integrating Active Directory with existing systems and applications. The goal is to streamline identity and access management across HBT’s network.Outcome
The successful completion of the HBT Active Directory project will result in a fully operational and secure AD environment tailored to HBT’s needs. This environment will provide centralized management of user accounts, streamlined authentication processes, and effective control over access to network resources. Key outcomes will include a structured AD hierarchy, configured group policies, and seamless integration with existing IT systems. The project will also deliver comprehensive documentation and training for HBT’s IT staff to manage and maintain the AD infrastructure efficiently.Problem Solved
The HBT Active Directory project addresses several critical challenges in network and user management. It consolidates user management into a single, centralized system, reducing administrative overhead and minimizing the risk of inconsistent security policies. By implementing group policies, the project enforces uniform security settings and compliance across the organization. The integration of AD with existing systems enhances overall efficiency and user experience. Additionally, the project mitigates risks associated with data loss and recovery by establishing robust backup and recovery protocols. Overall, the Active Directory solution provides HBT with a scalable and manageable infrastructure for controlling access and safeguarding network resources.
HTB ACADEMY| Windows Event Log Analysis and Threat Detection

Scope
The HBT Event Logs and Threat Detection project focuses on enhancing HBT’s ability to monitor, analyze, and respond to security events and potential threats within their IT environment. The scope includes the implementation of advanced event logging mechanisms, integration of a centralized log management system, and deployment of threat detection tools. The project will involve configuring log collection, setting up real-time alerting systems, and establishing procedures for analyzing and responding to security incidents. The aim is to improve HBT’s security posture and incident response capabilities.Project Description
The HBT Event Logs and Threat Detection project will start with an evaluation of HBT’s existing logging and monitoring infrastructure. Based on this assessment, the project will involve the deployment of a centralized log management system (such as a Security Information and Event Management (SIEM) solution) to collect, store, and analyze event logs from various sources including servers, workstations, and network devices. The project will also include configuring real-time alerts for suspicious activities and potential threats. Integration with threat intelligence feeds will be established to enhance detection capabilities. Additionally, the project will involve developing procedures for log analysis, incident response, and reporting to ensure timely and effective handling of security events.Outcome
The outcome of the HBT Event Logs and Threat Detection project will be a robust and integrated logging and threat detection system that significantly enhances HBT’s security monitoring capabilities. This system will provide centralized collection and analysis of event logs, real-time alerts for potential threats, and actionable insights into security incidents. Key deliverables will include a fully operational SIEM solution, configured alerting mechanisms, and detailed documentation on log management and incident response procedures. The project will also include training for HBT’s IT and security teams to effectively utilize the new tools and processes.Problem Solved
The HBT Event Logs and Threat Detection project addresses several key issues related to security monitoring and incident response. It resolves challenges associated with fragmented log management by consolidating event logs into a centralized system, enabling more efficient analysis and correlation. The project enhances threat detection capabilities through real-time alerts and integration with threat intelligence, allowing for quicker identification and response to potential security incidents. By establishing standardized procedures for log analysis and incident handling, the project improves overall security posture and helps HBT mitigate risks associated with cyber threats and data breaches.




